Blaster
Box Description
A blast from the past!
NMAP
- [IIS Windows Server: 80] [RDP: 3389]
Nmap scan report for 10.10.155.185
Host is up (0.081s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: IIS Windows Server
|_http-server-header: Microsoft-IIS/10.0
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: RETROWEB
| NetBIOS_Domain_Name: RETROWEB
| NetBIOS_Computer_Name: RETROWEB
| DNS_Domain_Name: RetroWeb
| DNS_Computer_Name: RetroWeb
| Product_Version: 10.0.14393
|_ System_Time: 2022-10-10T02:38:52+00:00
| ssl-cert: Subject: commonName=RetroWeb
| Not valid before: 2022-10-09T02:36:59
|_Not valid after: 2023-04-10T02:36:59
|_ssl-date: 2022-10-10T02:38:54+00:00; -5s from scanner time.
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -5s, deviation: 0s, median: -6s
FFUF
- Blog Website: [IP:80/retro]
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
________________________________________________
:: Method : GET
:: URL : http://10.10.155.185/FUZZ
:: Wordlist : FUZZ: Dirbuster/directory-list-2.3-medium.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
retro [Status: 301, Size: 150, Words: 9, Lines: 2, Duration: 153ms]
Content Discovery
- Wade Blog Website: [IP:80/retro]
- Searching Through
WadePosts: [IP:80/retro/index.php/author/wade]
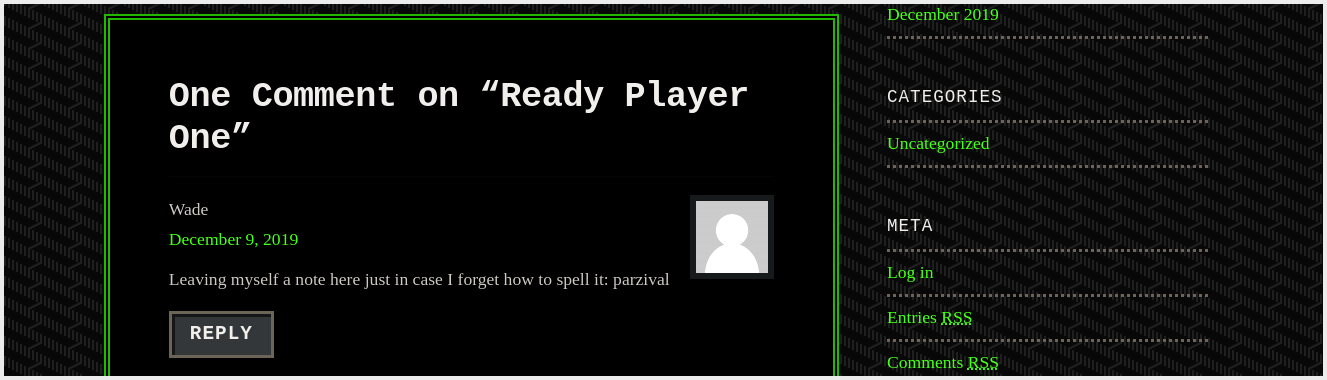
- [IP:80/retro/index.php/2019/12/09/ready-player-one]
- Found
WadeRDP (Remote Desktop Protocol) Credentials. - Username - Password: Wade:parzival
HHUPD
A Privilege Escalation Vulnerability exists in the Windows Certificate Dialog (CVE-2019-1388).